Number Verification APIs (1.0.0)
Service Enabling Network Function API to verify that the provided mobile phone number is the one used in the device. It verifies that the user is using a device with the same mobile phone number as it is declared. It also makes it possible for a Service provider to verify the number itself by returning the phone number associated to the authenticated user's access token.
In this API phone number term refers to the mobile phone number
This enables a Service Provider (SP) to verify the phone number of the mobile device being used to access their service where the mobile device is accessing the service provider over a mobile network (WiFi connections are out of this API scope). This can happen either by getting the comparison result or receiving the phone number of the device that is used, so they can verify it themselves.
This API currently provides two endpoints where both require a 3-legged token and authentication via mobile network (excluding for example by SMS/OTP or user/password as an authentication method):
- The first one checks if the user mobile phone number matches the phone number associated with the mobile device. It can receive either a hashed or a plain text phone number as input and it compares the received input with the authenticated user's phone number associated to the access token in order to respond true/false.
- The next one retrieves the phone number associated to the user's token and returns it so the verification can be made by the service provider.
Number Verification API uses the standard OAuth2 Authorization Code grant. The following diagram will help to clarify the end-to-end process, including previous steps prior to this API call.
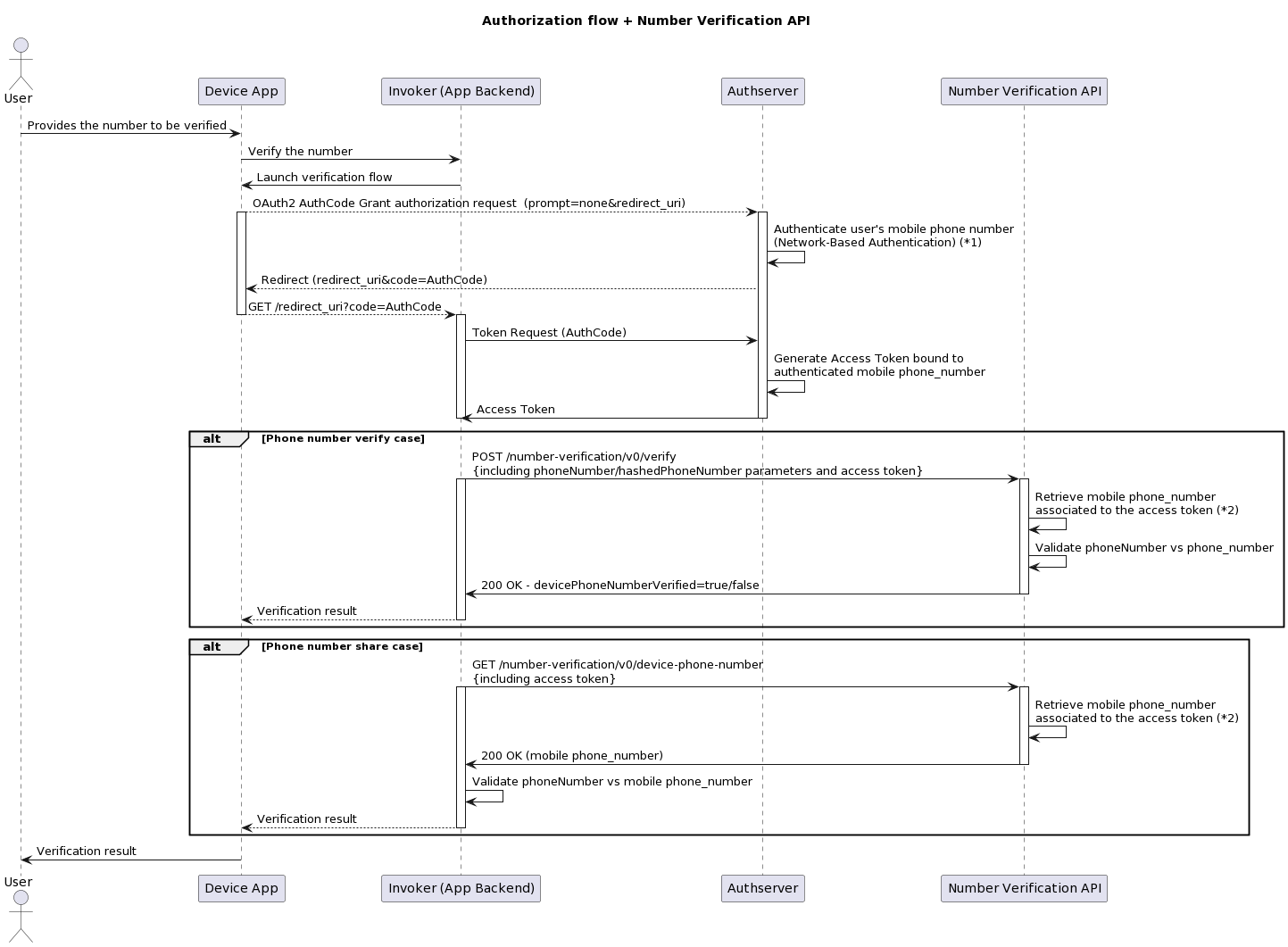
Additional details:
(1): Authentication must be automatic without any user interactions. Authentication methods such as SMS OTP or user/password are incompatible, as the goal is to validate the mobile phone number that is accessing the App. So it is required to be authentication via mobile network and without the user being involved. the use of parameter prompt=none, as described in OIDC Connect, ensures no user interaction.
(2): The way in which the phone_number is retrieved depends on the implementation. For example, access token may be a self contained encrypted JWT, so API can decrypt and identify phone_number. Some other implementations might request the phone_number associated to the token from Authserver.
https://developers.opgw.u.com.my/_mock/number-verification/number_verification/
https://silent-auth.u.com.my/
https://api-sandbox.opgw.u.com.my/
“Basic “ + base_64_encode (client_id + “:” + client_secret)
The request to the token endpoint must be sent using the HTTP POST method and have parameters populated in accordance with the rules.
Redirect URI value to where user want to redirect. This has to be same as what is given in the auth request.
This parameter commonly used in OAuth 2.0 and OpenID Connect protocols to specify the type of client assertion being used for authentication in a client-server interaction.
The client_assertion is a security measure used in authentication processes, especially within OAuth 2.0 and OpenID Connect, to authenticate the client (such as a web application, mobile app, or service) to an authorization server.
- Mock server
https://developers.opgw.u.com.my/_mock/number-verification/number_verification/ac/auth-service/openIDConnect/deviceinitiated/v1/token
- Testbed Authentication
https://silent-auth.u.com.my/ac/auth-service/openIDConnect/deviceinitiated/v1/token
- API Sandbox server (uses test data)
https://api-sandbox.opgw.u.com.my/ac/auth-service/openIDConnect/deviceinitiated/v1/token
- curl
- JavaScript
- Node.js
- Python
- Java
- C#
- PHP
- Go
- Ruby
- R
- Payload
curl -i -X POST \
https://developers.opgw.u.com.my/_mock/number-verification/number_verification/ac/auth-service/openIDConnect/deviceinitiated/v1/token \
-H 'Authorization: Basic d3lCOHF1R0RPWTdXTnUyVUV2eGF5Sk9aNVpTSU1KM1Y6V2ZHQUJqSUJpRDIySg==
' \
-H 'Content-Type: application/x-www-form-urlencoded' \
-H 'x-correlator: string' \
-d code=string \
-d redirect_uri=string \
-d grant_type=string \
-d client_assertion_type=string \
-d client_assertion=string \
-d code_verifier=stringOK If the token request is successfully completed (i.e. without error), an acess_token is returned by Gateway, in an HTTP 200 response in json payload with parameters.
OAuth 2.0 access_token used to gain access to the end-user information. This token CANNOT can be reused
The timeout available to make a request to the token endpoint. i.e. The request must be made before the “expires_in” time is reached.
Expiration time of the Access Token in seconds since the response was generated.
{ "access_token": "dUk4Bs0qgKQKujbGxQDvIdXkI6Bz", "token_type": "Always \"Bearer\"", "expires_in": 3599, "refresh_token": "eyJraWQiOiJ0ZXN0IiwidHlwIjoiSldUIiwiYWxnIjoiUlMyNTYeyJpc3MiOiJodHRwczovL2FwaXN0YWdpbmdyZWYuZGV2ZWxvcGVyLnZvZGFmb25lLmNvbSIsInN1YiI6ImRhNTNhOWRlLTljMmQtNGZkYy1hODY1LWE4OWZiZThmZGE2MyIsImF1ZCI6ImJSdlJKZVBHaGlMQndmelJSdEx3Z3REVFZ4UFdSQU1BIiwiZXhwIjoxNjA2OTE2Mzc2LCJpYXQiOjE2MDY5MTI3NzYsImF1dGhfdGltZSI6MTYwNjkxMjc1Niwibm9uY2UiOiI0NTI1OTUtOWRhMS00NDZiLWE0MmEtMWJkZmJmMTRhOGJjIiwiYXRfaGFzaCI6Ik9FRkZRVFpCTURCQ09FTkJRVVZFT0RnMU1qRTRSalJCUXpaQ1FUVXdRa1E0TWtRM1JFSTVSamsyT1RVMVJEbERPRE5GUkVFM05qa3hOVFl4UWpjM09BPT0iLCJhY3IiOiIwIiwiYW1yIjpbIk5PX0FVVEhOIl0sImF6cCI6IjU0NjEyNTk1LTlkYTAtNDQ2Yi1hNDJhLTFiZGZiZjE0YThhZiIsImhhc2hlZF9sb2dpbl9oaW50IjoiQUVBNkEwMEI4Q0FBRUQ4ODUyMThGNEFDNkJBNTBCRDgyRDdEQjlGOTY5NTVEOUM4M0VEQTc2OTE1NjFCNzc4In0.8Y4SArYeLdwyVUF7zjW9hyWTULiANn_MbvfXkxk62mKdPEeTI0HNOAG9tsItR1KVhHQdotAZOcoTNLRn66w4TMphQ1K2wfRcWTWKrTXtUA3Xuyx_bhZTkm7Zkz8k944JgpxejWgCjVUejlOiaQJZhu23UWufpd1An4x8UY7JU1LsKJj_OFMleESuM4xoJru0fPUkMMcNKB9D76sfBeSaZeMdqUARBhoWLyO_cb79sFfpu1Uf9V8SFB3NLRuktu0KANwqipwc_5c4LtxzP_rw3A_hWcaGpT67Qk1-tisW6ITCvrFKzZ5aqn8qWPEcte-XGoCXwd7pp0HKzgd1G8xw", "id_token": "dUk4Bs0qgKQKujbGxQDvIdXkI6Bz" }